Solutions
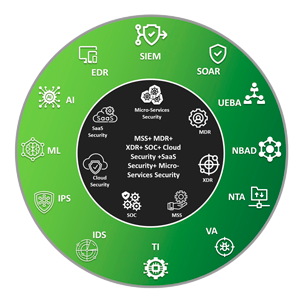
The threat landscape is constantly evolving and it is not only necessary to develop a capability to detect existing and emerging threats, but also to develop remediation strategies that provide a safe working environment for our Customers' users. With the above mentioned words in mind. VLATAM has experts who, through state-of-the-art technology, detect and determine the criticality of a threat.

Identify with a couple of clicks if you are vulnerable to new ransomware to take informed action. Measure the progress of your remediation efforts. All in a matter of hours.

It will allow you to know and measure the access routes that exist in your network to reach internal equipment or areas that should not have access. You will also be able to integrate information on your vulnerabilities.

You will know if your website, IP address or emails are on a list of planned attacks. Know if your RRSS, web, etc., are cloned. Analyze the behavior of your website and social networks or those of your interest.
Solutions
PERIMETER SECURITY:
Network attacks and data loss have a great impact not only on a company's image but also on its performance and progress .....
WEB SECURITY:
Protection against cyber-attacks in seconds without slowing down your website, secures your websites, APIs and web applications. Flexible web protection that gives a ....
MAIL SECURITY:
Protection against threats from impostors and vendor fraud, detect and block advanced malware, identification of at-risk users (VAP), detection of .....
NETWORK SECURITY:
Not all users connecting to the network should have access to all resources. To prevent possible attacks or transmission of malicious code, .... should be identified.
ENDPOINT SECURITY:
We provide technologies for end-to-end device management and security and endpoint security.......
SECURITY OF UNSTRUCTURED DATA:
Data are of different types and are distributed and must be protected against malicious and accidental threats, regardless of the location on the network......
DATABASE SECURITY (STRUCTURED DATA):
No need for agents or hardware, software-based compliance information and database security platform ....
SECURITY AND ACCESS MANAGEMENT:
Manages digital identities and user access to an organization's information, systems and resources, administers who.....
ACTIVE DIRECTORY AUDITING AND MANAGEMENT:
Provides a clear picture of all changes made to your AD resources, including AD objects and their attributes, helps manage, detect and ......
CONTINUOUS VULNERABILITY MANAGEMENT:
Understand your risk and know which vulnerabilities to fix first. Get cloud-based or on-premise vulnerability management for visibility.....
INTRUSION TEST SOFTWARE:
Attackers are always developing new vulnerabilities and attack methods: penetration testing software will help you use your own weapons. ....
ADVANCED THREAT HUNTING:
Designed for both security analysts working in dedicated SOC teams and IT administrators, CISOs etc. ....
FORENSIC ANALYSIS
Tools for computer forensics, mobile and cloud. It can help you acquire and analyze a wide range of mobile devices, run several....
CYBERINTELLIGENCE:
Protect your business from cyber threats, identity theft, brand impersonation and fraud beyond the perimeter. Our platform will alert ....
CYBERSOC SERVICE
Protect all your digital assets, people and networks 24 hours a day, with advanced real-time threat detection and automatic correction with machine learning.